Last Updated on March 12, 2017
Just as technology has taken over payments and fund transfer through online transactions, cyber chairmen are also doing theirs by exploiting people’s data and transaction details using fake technical support as a defense.
This could be a kind of advancement for these cyber chairmen because their method on invasion is somewhat improving from local network airtime transfer to next level. With more and more people worldwide preferring online transactions, cyber criminals are using the ‘fake technical support’ model to steal consumer data, reported by security software firm Symantec, India. Let me give you two eye opener as you read.
Have you received this message above? And if you happened to have responded well, i believe you must have been scammed. I wrote a post on mobile network scam alert where you will be swayed to send recharge card in a so format and also La casera of a thing promo. These are just the works of the bad guys season 3!
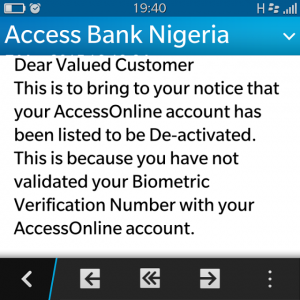 |
| BVN scam sms |
These bad guys have also gone tech wise. Sometime they send fake warning messages to devices like smartphones about phone being at risk to virus and needed to quickly click and install their recommended free anti-virus. Once you clicked to install, scanned, they might sniff out your contact details, text messages, google logs etc to their server. This calls for apps permission. Permission is a given a room to take advantage of a resource it was declared “permitted” and that is why it is always recommended to avoid 3rd party apps, untrusted free apps, cracked apps and monitor permissions using some utility apps.
If we could reiterate on the first paragraph, These bad guys have extensive resources and a highly-skilled technical staff that operate with efficiency. If you a regular guy in online transactions, i think you should not use public WiFi and cyber cafe. You might be sitting beside someone that pretends to be serious and immediately your timer finishes, he switches over to your computer in complaint of his computer hanging always. His next step will be to view saved passwords and username. In the case of a good Samaritan that share WiFi, he might be injecting commands to all his beneficial users and maneuvering with their information.
You might be crying for a secured way. There is no guaranteed way to be invincible from the bad guys but there are certain precautions one should be accustomed to.
- Limit the amount of personal information you share on social networks, including login information, formal email address and birth dates.
- Use strong password in other to limit brute-force attacks. Avoid simple English word instead use alphanumeric characters (“$#pass7&ero1”) and make sure to change them at least 5 times a year.
- Mind email subscription you are following. Do not just enter your email in the name of getting tips, make money idea, download link promises.
- For attachments especially from junk mails, you should be careful with them. If you happen to click ads from porn images, that is a broad street for your demise. Do not click on any link you see on Facebook. Facebook will not guarantee your privacy. Your friend’s account might have been hacked just because they like to click on any enticing links.
Stay safe and be wise!


4 responses to “Cyber invaders use fake technical support to steal data”
No, it is not
Thanks
Nice.. I always saw mtnbetterme.. Is it true
Thanks for the idea